In today’s digital era, cyber threats such as ransomware attacks and phishing scams can strike anyone at any time. For families and businesses, the risk of financial loss, identity theft, and reputational harm is real and ever-increasing. As cyber insurance evolves, it offers essential protection and peace of mind by providing a financial safety net and expert recovery support when digital attacks occur. At Torian Insurance, our 100 years of local expertise mean we understand your unique needs and are committed to providing customized insurance solutions that protect what matters most to you.
The Growing Need for Cyber Insurance
Cyber threats impact everyone—from small business owners to households managing personal accounts online. With more daily tasks and transactions moving into the digital space, vulnerabilities also increase.
Recent trends show that:
- Ransomware attacks are locking businesses out of critical data.
- Phishing scams trick individuals and employees into revealing sensitive information.
- Data breaches can lead to severe financial losses and long-term damage to reputation.
According to IBM’s 2024 Cost of a Data Breach Report, organizations with robust incident response plans and cybersecurity measures can reduce these costs by an average of $2.2 million, highlighting the importance of proper planning and coverage.
Small businesses often have fewer cybersecurity defenses, making them prime targets, while families face personal hardships if their data is compromised. Cyber insurance fills the gap between prevention and recovery, ensuring that when an incident occurs, you have the financial support to get back on track.
What’s Covered by Cyber Insurance?

Modern cyber insurance policies are designed to help you manage the financial aftermath of a cyber incident. While specifics can vary by provider, most policies include coverage for the following:
- Data Restoration and Recovery
- Costs to restore or recover lost or corrupted data.
- Professional services to remove malware and repair affected systems.
- Legal Support and Regulatory Costs
- Coverage for legal fees, settlements, and fines related to data breaches.
- Assistance with issues surrounding credit fraud for individuals.
- Notification of individuals who may have had their data compromised.
- Business Interruption
- Compensation for lost income and operational expenses during a cyberattack. Learn why business interruption coverage is crucial.
- Reputational Damage and Crisis Management
- Services to help manage public relations and restore trust, aiding both businesses and families in returning to normal operations.
- Emerging Coverages
- New policy features that address evolving risks such as biometric data misuse, smart home vulnerabilities, and personal cyber extortion.
These coverages are carefully designed to address both immediate recovery costs and longer-term financial implications of cyber incidents. For instance, consider a small family-owned restaurant that manages its reservations online and processes credit card payments daily. If a hacker gains access to their payment gateway, the costs could include forensics to identify the breach, legal fees to handle customer notifications, and restoring compromised data. A robust cyber insurance policy can help fund these expensive efforts and protect the owners from devastating financial losses. Real-life scenarios highlight how seemingly minor oversights—like failing to install a simple software patch—can lead to serious threats.
It is also noteworthy that many insurers today provide access to network security experts or pre-incident support. This collaboration helps policyholders identify vulnerabilities and create contingency measures before any attack happens. By understanding what is covered, policyholders can better prepare for potential scenarios while ensuring that any gaps in coverage are minimized.
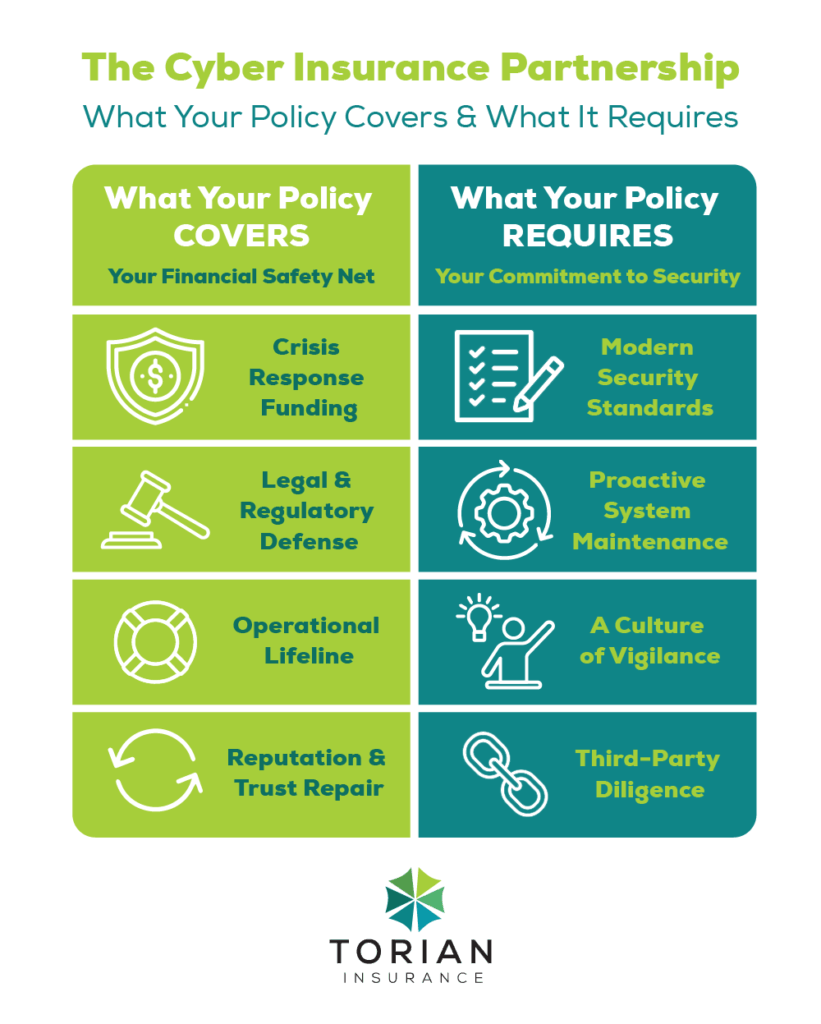
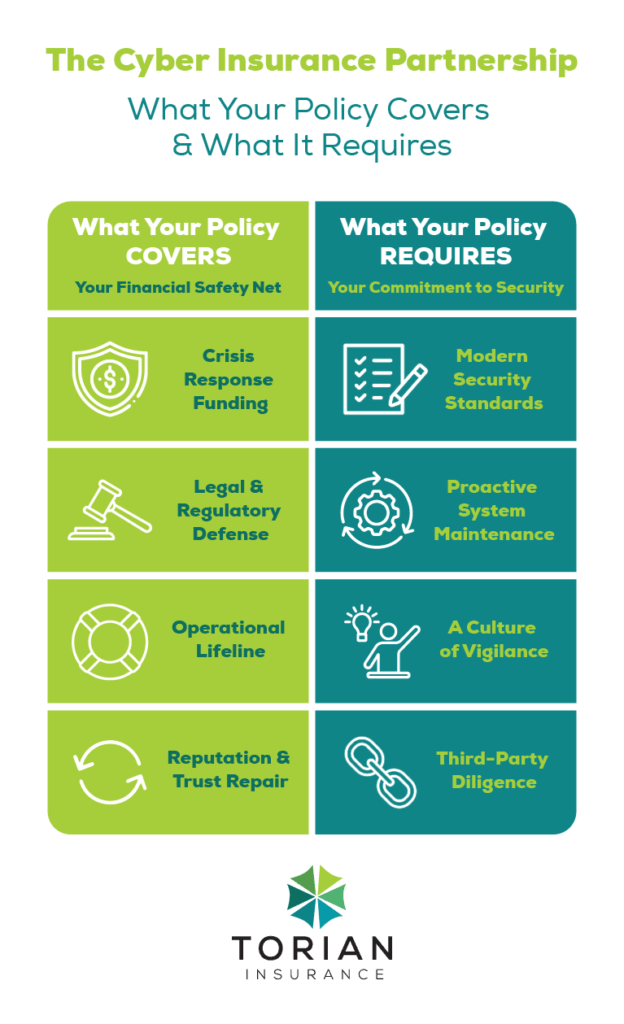
Common Exclusions and Coverage Gaps
It is important to understand that not every incident is covered. Key exclusions often include:
- Non-Compliance with Security Standards: Policies may require measures like multi-factor authentication or regular system updates. Failure to follow these protocols can lead to claim denials.
- Outdated Technology: Breaches involving unsupported software or outdated systems are typically excluded.
- Negligence or Poor Cyber Hygiene: Weak passwords or a lack of security training can result in claims being rejected.
- Third-Party Vulnerabilities: If the breach is caused by an external vendor’s insecure practices, coverage might be limited or unavailable.
For example, imagine a local accounting firm that uses unsecured file-sharing tools to exchange sensitive documents. If their client data is leaked due to these vulnerabilities, the claim might be partially or wholly denied based on the firm’s failure to maintain proper security. As technology rapidly evolves, businesses and individuals must act proactively to align with an insurer’s standards. Review your policy carefully and ensure your cybersecurity practices meet or exceed the requirements. Understanding these exclusions is crucial for setting the right expectations and determining where additional investments may be necessary.
How to Choose a Policy and Prepare for Coverage
Selecting the right cyber insurance requires a dual focus: finding a policy that fits your unique risks and demonstrating that you are a responsible partner in mitigating them. By carefully evaluating policy details while actively strengthening your defenses, you can secure comprehensive and affordable coverage.
Evaluate Your Policy Options
Start by assessing these key policy considerations:
- Evaluate Coverage Limits: Estimate the potential financial impact of a cyber incident on your household or business. Choose a coverage limit that provides a comfortable safety margin without over-insuring.
- Understand Incident Response Requirements: Look for clear guidelines on the steps required after a breach. Ensure you can meet protocols such as timely notifications and having an established incident response plan.
- Assess Provider Expertise and Customization: Seek an insurer that offers tailored policies to address your specific vulnerabilities. Talk to our local team about designing policies that fit your unique situation, as a one-size-fits-all approach is rarely effective.
- Examine Exclusions and Security Mandates: Read the fine print to understand any necessary cybersecurity practices your insurer requires. This helps you avoid claim denials and identifies where you may need to improve your security posture.
- Plan for Future Threats: Choose a policy that adapts to evolving cyber risks. As state and national regulations change, a forward-looking policy will remain effective as new laws and standards are introduced.
Strengthen Your Defenses to Secure Better Terms
Insurers increasingly reward proactive clients with more favorable terms and lower premiums. To position yourself as a low-risk partner and qualify for the best coverage, focus on these critical actions:
- Use Multi-Factor Authentication (MFA): This is non-negotiable in today’s environment. Add this second layer of verification in addition to passwords to deter the majority of common hacking attempts.
- Keep Software Updates Current: Regularly update all software, applications, and operating systems. This closes known security gaps that hackers actively exploit.
- Conduct Regular Cybersecurity Training: Educate everyone in your household or organization to recognize phishing attempts, use strong, unique passwords, and practice safe browsing habits.
- Develop an Incident Response Plan: Don’t wait for an attack. Outline the exact steps to take immediately after detecting a breach, including who to notify and how to isolate affected systems.
- Perform Risk Assessments: Periodically evaluate your digital vulnerabilities. For businesses, this includes monitoring the security practices of third-party vendors who have access to your data.
- Stay Informed About Evolving Threats: Use trusted resources, like those from the National Cybersecurity Alliance, to stay current on emerging threats and protective measures.
These measures do more than just satisfy an insurer—they create a resilient foundation that can significantly reduce the likelihood of an attack and ensure a swift recovery if one occurs.
Beyond the Policy: Building a Resilient Cyber Strategy
Cyber insurance is a critical financial safety net, but it works best as one integral component of a broader, proactive cybersecurity strategy. A truly resilient defense is layered, combining robust prevention measures with a vigilant culture and a plan for recovery.
The first layer is proactive prevention. This includes the essential technical defenses—such as firewalls, antivirus software, and intrusion detection systems—that protect your digital perimeter. However, since technology alone is not foolproof, the second and most crucial layer is a culture of cyber resilience. This is built through continuous learning and regular training that empowers everyone in your household or organization to become a human firewall. By sharing best practices and fostering an environment where people can recognize threats like phishing, you significantly reduce the risk of a breach caused by human error.
Finally, cyber insurance serves as the third essential layer, providing financial support and access to expert recovery services—including digital forensics and legal consultation—when other defenses fail.
This holistic strategy is most effective when woven into your broader planning:
- For Businesses: this means aligning cyber insurance with operational continuity plans and disaster recovery initiatives, supported by regular risk assessments to monitor for new threats.
- For Families: it involves integrating cyber insurance with financial planning and digital asset management, where proactive steps like credit monitoring complement the financial protection a policy provides.
When these elements—prevention, culture, and insurance—work in concert, you move beyond simple protection. You build a robust defense that minimizes disruption and helps you weather the complexity of today’s cyber threat landscape.
Navigating the Cyber Insurance Claims Process
Understanding the cyber insurance claims process can be as important as selecting the right policy. When a cyber incident occurs, timely and efficient claims handling is critical to minimizing downtime and restoring operations. Here are some practical insights:
- Promptly report any incident to your insurer as soon as it is detected. Provide detailed information about what systems were affected, the scope of the breach, and any immediate mitigation steps taken. Maintaining clear records—such as incident response logs—bolsters your claim and streamlines the investigation process. Many policies also include specific time frames for filing a claim, so be sure to review and adhere to those deadlines to avoid denial or reduced coverage.
- During the claims investigation, digital forensics experts may examine the compromised systems to identify the cause and impact of the breach. Cooperation and clear communication with your insurer ensure you receive the support you need. Some policies may also require post-incident remediation measures—such as patching vulnerabilities or upgrading software—to qualify for full reimbursement. By following these guidelines thoroughly, you can expedite the process and bolster your chances of receiving full claim benefits.
Customized Cyber Insurance Solutions Businesses and Families

A one-size-fits-all approach does not work in managing cyber risks. Torian Insurance offers tailored solutions for both businesses and families:
For Businesses:
- Customized policies that address industry-specific risks and compliance requirements.
- Coverage for third-party exposures linked to external vendors.
- Flexible coverage limits, scalable based on your company’s size and scope.
For Families:
- Protection against identity theft and unauthorized access to personal data.
- Support for emerging risks affecting smart home devices.
- Policies designed to address everyday digital exposures without unnecessary add-ons.
Our community-focused approach ensures every policy meets the distinct challenges faced in Southern Indiana, Illinois, and Kentucky. With decades of local expertise, we stay ahead of regional trends and provide solutions that adapt as the digital landscape evolves. For example, as families increasingly adopt interconnected smart home systems for convenience, many insurers are adapting their policy offerings to better address vulnerabilities in these devices.
Looking Ahead: The Future of Cyber Insurance
As new technologies become integral to daily life, cyber risks will continue to evolve. Artificial intelligence (AI) has the potential to improve threat detection and automate responses, but it also introduces complexities in coverage. Additionally, the growing popularity of Internet of Things (IoT) devices means more entry points for hackers seeking to exploit personal and commercial networks. Policies will likely adapt to address AI-driven attacks, deeper supply chain exposures, and newly identified vulnerabilities in smart devices, from home appliances to industrial equipment.
Legislation and regulatory guidelines around data privacy and cybersecurity will also sharpen the parameters of coverage. State-level mandates might set standards for breach notifications, training requirements, or minimum compliance benchmarks. Staying up to date on these legal obligations can help policyholders secure the best possible protection. The dynamic nature of these developments makes it crucial to rely on an insurance partner who remains informed, proactive, and ready to adjust coverage to new norms.
Embracing Cyber Insurance: Safeguard Your Future Today
Businesses and families face a continually evolving range of cyber threats. Cyber insurance provides essential financial safeguards to recover from incidents like ransomware attacks or data breaches, but it works best in tandem with robust security measures and a holistic risk management strategy.
At Torian Insurance, our deep commitment to community and extensive local expertise guide us in providing personalized solutions that protect you today and adapt for tomorrow. Don’t wait until a crisis unfolds—take the first step toward better protection and contact Torian Insurance to secure the peace of mind you deserve.



